What is Advanced Endpoint Protection?
Advanced Endpoint Protection refers to the security solutions that are used to address issues about endpoint security. Thus, Advanced Endpoint Protection can be defined as securing and protecting endpoints against all kinds of attacks, zero-day exploits, and those inadvertent data leakages that happen due to human errors.
Advanced Endpoint Protection is what helps prevent targeted attacks and APTs ( advanced persistent threats), which can't be prevented using antivirus solutions alone. Advanced Endpoint Protection solutions provide enterprises with a full spectrum of security solutions that can be managed centrally and which help secure endpoints- servers, workstations, etc connected to endpoints, plus the many endpoint devices.
Why Xcitium Advanced Endpoint Protection Software?
Advanced Endpoint Protection or Endpoint Security fosters solutions to protect and secure the endpoints from zero-day exploits or unknown malware or advanced persistent threats. Conventional Antivirus cannot be a standalone Advanced Endpoint Protection solution to drive out the adamant threats, with that in place, Advanced Endpoint Protection took its form to deliver absolute.
Advanced Endpoint Protection solutions ensure complete data protection for enterprises. Advanced Endpoint Protection delivers centralized security solutions to secure workstations, servers, and devices that are connected to access enterprise networks.
Advanced Endpoint Protection Platforms and Enterprise Security
Advanced Endpoint Protection Platform (EPP) is an integration of antivirus, firewall, anti-spyware, and application control featuring host intrusion prevention techniques - all in one single platform. It would be defined more comprehensively when additional security measures like patch management, vulnerability assessment, and configuration capabilities are incorporated for better and proactive protection. Advanced Endpoint Protection ensures the prevention of malware attacks and processes the protection of data files and disk encryption and device management which may be the best deal to empower Enterprise Security.

How Xcitium AEP can prevent your Advanced Endpoint Protection from Ransomware Attack
Xcitium has this Containment technology that prevents viruses to take control of the system. This unique technology creates a virtual environment, registry, hard drive, and even a virtual COM interface. If the malware happens to sneak into your computer, its Advanced Endpoint Protection will continue to perform its nefarious activity in the virtual environment. Your Advanced Endpoint Protection system's original documents and files will not be infected. Xcitium's Containment technology just keeps a tab on all kinds of infections.
How Advanced Endpoint Protection Works? Default Deny Security with Default Allow Usability
Xcitium Advanced Endpoint Protection prevents unknown malware from running on your endpoints with our revolutionary Default Deny Platform™. Our patent-pending CPU-enforced OS virtualization technology enables you to run a viable Default Deny Security Posture—where unknown files are automatically laced in a lightweight virtual container on the Advanced Endpoint Protection and analyzed in real-time.
Your Advanced Endpoint Protection is 100% malware free with a viable Default Deny Security Posture. You can manage and protect any device, whether it's on or off your company network with Xcitium Advanced Endpoint Protection.
The forensic analysis returns a verdict on unknown files in about 45 seconds. Good files are allowed to run on the endpoint CPU and malware files are removed. The Advanced Endpoint Protection virtual client uses negligible CPU resources and users can open unknown files safely in containment, so productivity continues.
One Suite Delivers Complete Endpoint Protection
Lightweight Endpoint Protection Client, Forensic Analysis and Unified Management
Xcitium Advanced Endpoint Protection quarantines all the unknown files in a virtual container - where the suspicious files can be analysed and executed safely and instantly. Xcitium AEP includes a Default Deny Platform to focus on complete enterprise visibility while the endpoints connected over the organization's network are malware free. It also includes a console of IT and security management to help manage Windows, Linux, OSX, iOS and Android devices connected to all the virtual and physical networks.
Xcitium Client - Advanced Endpoint Protection
Endpoint Protection - Cloud Based Sandbox, static and dynamic analysis
Combines the complete coverage of our Default Deny Platform in a lightweight endpoint virtual client (only 10MB), deployed and managed by our unified management platform. Using the strengths of our digital signature-based whitelist and malware blacklist, and automatic containment for unknowns—our Default Deny Platform prevents malware from executing on your endpoints. Automatically, VirusScope AI/Machine Learning provides a local verdict of unknown files and, to accelerate verdicts, unknown files are sent to Valkyrie for simultaneously.
Xcitium Valkyrie™ - Advanced Endpoint Protection
Analyzes the 73 billion file queries and 300 million unique unknown files that are submitted annually. Static and dynamic file behavior Advanced Endpoint Protection analysis and, when needed, expert human analysis, provide accelerated verdicts for approximately 200 million known and 1 million unique, unknown files every day. Forensic intelligence helps you predict your attack's next move for a proactive defense.
ITSM brings all your Advanced Endpoint Protection management needs together-including the remote provisioning, configuration, and control of Android, iOS, and Windows devices-into a unified SaaS platform that streamlines operations and reduces risks from the limited visibility and potential security gaps of multiple point products and management tools.
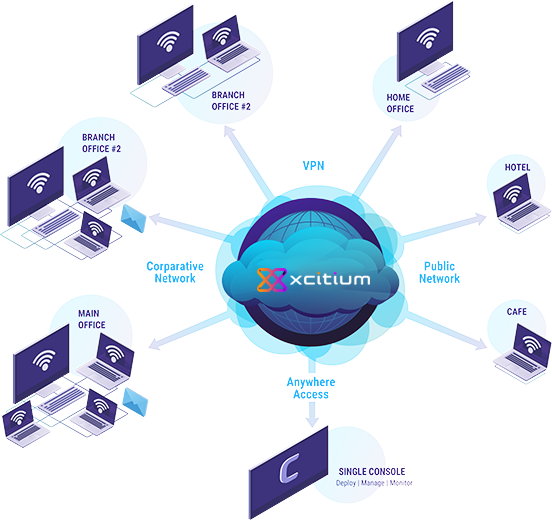

Complete Protection, All in One, Advanced Endpoint Protection Security Solution
Xcitium AEP secures all your servers, desktops, laptops, and mobile devices from known and unknown malware-without requiring signatures or updates. And, it supports Android, iOS, Windows or Linux systems, regardless of the type or age of the endpoint hardware.
You can see and manage everything though the single dashboard of our unified management platform.
